
2020 Agenda
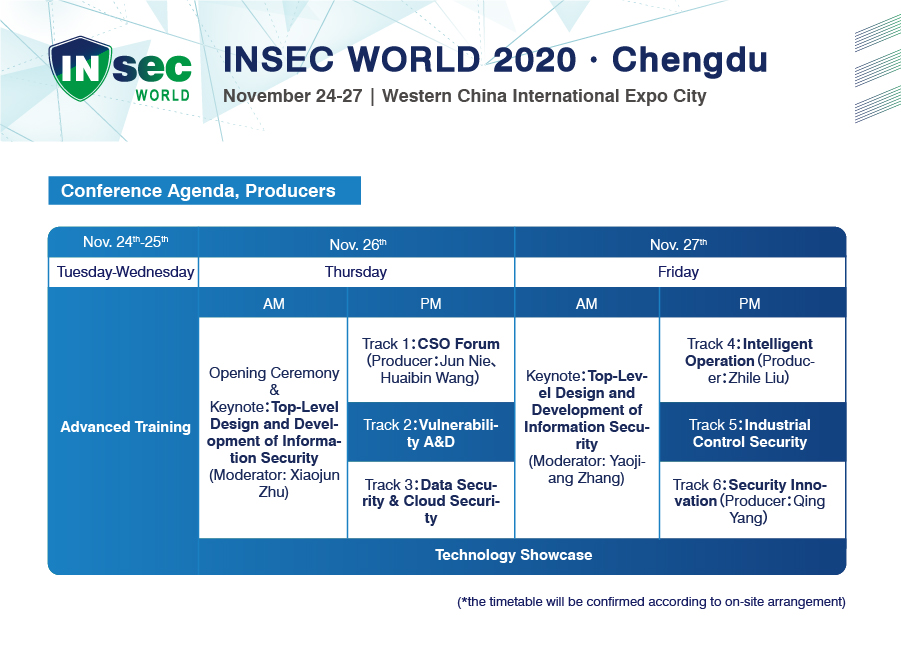
| Day One 26 November,2020 (Thursday) | |||
| Time | Hall 9, Western China International Expo City | ||
| 8:30-9:15 | Registration&Networking Breakfast | ||
| 9:15-9:30 | Opening Ceremony | ||
| Keynote Moderator: Xiaojun Zhu |
|||
| 9:30-10:00 | New Infrastructure Security Challenges and Build-in Security Highlights Jiangxing Wu |
||
| 10:00-10:30 | Trusted Network Architecture Based on Blockchain Dr. Jie Li |
||
| 10:30-10:50 | Cyber Security in Today’s World Christophe Poisson |
||
| 10:50-11:00 | Tea Break | ||
| 11:00-11:20 | Drive “Security Native” into Fabric of Hybrid Cloud Business Liang Feng |
||
| 11:20-12:20 | Hacker TALK
Panel Discussion: China’s 【First Generation White Hat】 Hacker TALK Moderator: Quan Peng (PP) Guests: Wei Gong (goodwell), Xin Huang, Ben Ji, Yong Lin (Lion), Junqing Wang (la0wang), Zhaoxia Xie (Frankie), Xundi Zhang |
||
| 12:20-12:40 | Norms of Responsible State Behavior in Cyberspace John Davis |
||
| 11:45-13:30 | Lunch | ||
| Conference Room A | Conference Room B | Conference Room C | |
| Track A:CSO (Moderator:Bin Wang) |
Track B:Vulnerability A&D and Security Research (Moderator:Lisa Zhang) |
Track C:Data Security & Cloud Security (Moderator:Wei Gu) |
|
| 13:30-14:00 | Towards Design and Implementation of Modern Security Infrastructure and Product Qidan He |
The Trend of Offensive and Defensive Technology and our Threat Hunting Capacity Building Practice Siming Pang |
Data Backup Technology Development in Hybrid Cloud Scenarios Xiaoqin Hu |
| 14:00-14:30 | Security Policy – Is Yours Built for DevOps Tony Li |
Zero-Trust: Reinventing the Concept of Cybersecurity Richard Li |
|
| 14:30-15:00 | The Practise of Trace and Retaliation in Red Team/Blue Team Exercises
Wei Guo |
A practice in anti-Bot under “New Infrastructure Construction” Lonny Li |
Research and Practice of Risk Assessment of Masked Data from the Perspective of Compliance Lei Chen |
| 15:00-15:15 | Tea Break | ||
| 15:15-15:45 | Infrastructure Security of Large-scale World-class Enterprises Brian Wang |
Cyberbit Range: Beginning of Efficient Cyber Security Blue Team Kevin Zhu |
To Harness Data to a New Infrastructure on the Basis of Security– To Build a Multi-dimension Data Security Framework for New Infrastructure Jie Zhou |
| 15:45-16:15 | Usable Security – Making Users a strong Link in Security Tiger Deng |
Use Fuzzing to Discover Vulnerabilities Related to the rdp Protocol Songlin Li |
Zero Trust Practice in Cloud-Native Applications Nicloe Zhang |
| 16:15-16:45 | Data Theft and Intelligence Detection of Isolated Intranet Rui Zhao |
||
| Day Two 27 November,2020 (Friday) | |||
| Time | Hall 9, Western China International Expo City | ||
| 9:00-9:30 | Registration&Networking Breakfast | ||
| Keynote Moderator:Yaojiang Zhang |
|||
| 9:30-10:00 | Public Blockchains: How can You Build one Ethically? Bill Roscoe |
||
| 10:00-10:20 | Build the Solid Foundation for Cybersecurity in the Era of New Infrastructure Steven Lin |
||
| 10:20-10:40 | Lighting it Up – Playbook Heat Maps Derek Manky |
||
| 10:40-10:50 | Tea Break | ||
| 10:50-11:10 | Don’t let the Attackers Weaponize Fear: Malware in the time of COVID-19 Diana Kelley |
||
| 11:10-11:30 | Analysis of Satellite System Security and New Ideas on Security Education of New Infrastructure Construction Qing Yang |
||
| 11:30-12:30 | Panel Discussion:CSO and Security Innovation Moderator:Yaojiang Zhang Guests:Feng Liu,Weichun Li,Xinkai Liu,Robin Wang,Joey Xiang |
||
| 12:30-13:30 | Lunch | ||
| Conference Room A | Conference Room B | Conference Room C | |
| Track D:Intelligent Security Operation (Moderator:Mingkun Yuan) |
Track E:Industrial Control Security (Moderator:Chenglin Lei) |
Track F:Security Innovation (Moderator:Qing Yang) |
|
| 13:30-14:00 | Security Operation Theory and Practice Po Hu |
Analysis of Security Threats and Hidden Dangers of IP Verification Enabled Industrial Internet Zhiguo Liu |
New Generation Formal Verification Technology with High Speed and Efficiency Guarantees No False Negative Long Li Gavin Bu |
| 14:00-14:30 | Next Generation Security Defense and Response Collin Chang |
Analysis of C2 Attack Chain Based on OPC DA Protocol Yang Hu |
Innovative Experience of Multi-port Visualization Technology for Security Business Xin Huang |
| 15:00-15:15 | Intelligent Security Operations under Digital Transformation Mingkun Yuan |
Industrial IoT System Security Practice Mcgill Wang |
Thoughts on Frontier Security Research in Enterprises Bo Zhang |
| 15:00-15:15 | Tea Break | ||
| 15:15-15:45 | Security Operation under Zero Trust Framework Yi He |
Security Analysis of IOV Platform Xianwen Fu |
Qiling Framework: Modern Reverse Engineering Experience Ziqiao Kong Chenxu Wu |
| 15:45-16:15 | AISecOps : Multi-dimensional and Scalable Alarm Evaluation for Enterprise Zijian Wu Fudi Wu |
Lost in Translation: When Industrial Protocol Translation goes Wrong Dr. Marco Balduzzi Philippe Lin |
Security Threats to AI×IoT Shuai Xie |
*The timetable will be confirmed according to on-site arrangement.